NEWNow you can listen to articles from various sources!
Dating platforms that claim to be discreet and private often fall short of expectations. A prime example is Ashley Madison, a site catering to individuals seeking extramarital affairs, which experienced a significant data breach in 2015. The breach resulted in the exposure of personal information, emails, and financial details of 32 million users, leading to public outcry, legal actions, and even reported suicides.
Recently, a dating safety app named Tea also faced a breach, compromising selfies, photo identification, and various images shared within the app.
Sign up for my FREE CyberGuy Report
Receive top tech tips, urgent security alerts, and exclusive deals directly in your inbox. Also, gain instant access to my Ultimate Scam Survival Guide – all for free when you subscribe to my CYBERGUY.COM/NEWSLETTER.
DIOR DATA BREACH EXPOSES US CUSTOMERS’ PERSONAL INFORMATION
Insights into the Tea data breach
Launched in 2023, Tea was positioned as a U.S.-based app focused on “dating safety” for women, initially requiring verification through selfies and official ID. Although the ID requirement was later removed, the app surged in popularity in July 2025, climbing to the top spot on the U.S. App Store and amassing millions of users.
On July 25, users on 4chan discovered a publicly accessible Firebase storage bucket containing Tea user data (via 404Media). A post on the forum allegedly exclaimed: “DRIVERS LICENSES AND FACE PICS! GET THE **** IN HERE BEFORE THEY SHUT IT DOWN!”
Subsequently, Tea confirmed that the breach involved unauthorized access to an older database containing around 72,000 images, including 13,000 selfies and ID photos, as well as 59,000 images from posts, comments, and messages. These belonged to users who signed up before February 2024.
Tea’s leadership publicly acknowledged the image breach, attributing it to data from outdated systems that had not been migrated to the current secure infrastructure. They also clarified that only legacy users were impacted and that no email addresses or phone numbers were exposed.
Further revelations from independent researcher Kasra Rahjerdi and 404 Media indicated that the breach extended beyond images, with approximately 1.1 million direct messages (DMs) from early 2023 through July 2025 also being exposed. These DMs contained sensitive discussions on topics like abortions, infidelity, contact details, and more.
WHAT IS ARTIFICIAL INTELLIGENCE (AI)?
In response, Tea disabled its DM feature and temporarily shut down the affected messaging system. The company reassured users that there was no evidence of intrusion into other parts of its infrastructure.
CyberGuy attempted to reach out to Tea for comments but had not received a response at the time of publication.
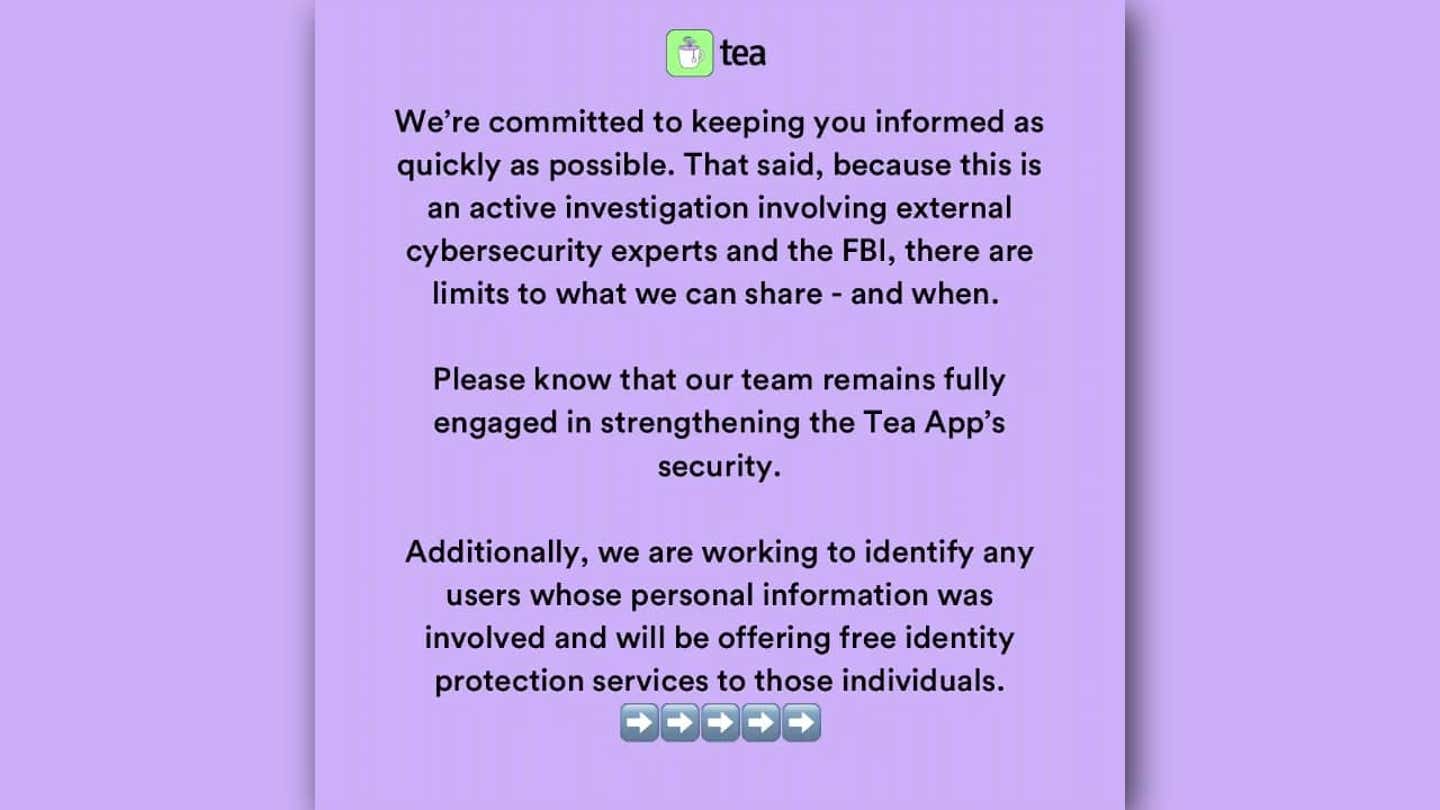
Tea app customer notice. (Tea)
The impact of the Tea app breach on users
The Tea data breach represents a nightmarish scenario for all users, highlighting the negligence of companies in safeguarding privacy.
Tea marketed itself as a secure platform for women to share personal experiences, only to falter in its fundamental promise of protecting user privacy.
This breach goes beyond mere usernames or email addresses. It involves government IDs, selfies, and 1.1 million private DMs containing confessions, relationship details, and deeply personal conversations on topics like assault and abortions. Once such images and conversations are exposed, the damage is essentially irreversible.
Unlike a generic social app, Tea positioned itself as a “dating safety” platform for women, implying a higher level of privacy protection. The leaked data initially surfaced on a misogynistic forum, subjecting victims to harassment, doxxing attempts, and unauthorized sharing of their stories and images.

A woman using an app on her smartphone. (Kurt “CyberGuy” Knutsson)
6 steps to protect yourself from the Tea data breach
If you have used Tea or registered on the platform, it is crucial to take immediate action. Here are six measures to enhance your privacy and mitigate the repercussions of the breach.
1) Enroll in identity theft protection services
If your ID was compromised in the breach, you may be vulnerable to identity theft. Identity theft protection services can help you stay vigilant against suspicious activities such as new credit inquiries or account openings, empowering you to address potential threats promptly.
Explore my recommendations and top choices for safeguarding against identity theft at Cyberguy.com/IdentityTheft.
2) Utilize a personal data removal service
Exposed selfies or personal information may surface on people-search websites or illicit databases. A personal data removal service can assist in erasing your personal data from the internet. While no service guarantees complete data removal, having such a service can aid in consistently monitoring and automating the process of eliminating your information from numerous sites over an extended period.
Discover leading data removal services and access a free scan to determine if your personal data is already circulating online by visiting Cyberguy.com/Delete.
Check if your personal information is already online with a free scan: Cyberguy.com/FreeScan.
ACCESS FOX BUSINESS ON THE GO HERE
3) Update your passwords and activate two-factor authentication (2FA)
Attackers often exploit reused usernames and passwords across different platforms, even if your login credentials were not part of the breach. Refreshing your passwords and enabling two-factor authentication on all accounts are basic yet critical defenses. Consider employing a password manager to generate and securely store complex passwords, minimizing the risk of password recycling.
Explore the top password managers recommended by experts in 2025 at Cyberguy.com/Passwords.
4) Stay vigilant against phishing and extortion attempts, and deploy robust antivirus software
Following high-profile breaches, victims often receive threatening messages. Refrain from responding, clicking on links, or engaging with the sender. Report the message and block the sender if you feel threatened. In case of safety concerns, reach out to local cybercrime authorities or digital rights organizations.
The most effective way to shield yourself from malicious links is by installing robust antivirus software across all your devices. This security measure can also alert you to phishing emails and ransomware scams, safeguarding your personal information and digital assets.
Access my top picks for the best antivirus protection solutions for Windows, Mac, Android & iOS devices in 2025 at CyberGuy.com/LockUpYourTech.
5) Monitor the dissemination of your images online
Leverage reverse image search tools like Google Images or PimEyes to track if your images have been shared elsewhere. Should you discover any unauthorized sharing, document the instances, report them to the platform, and refrain from direct engagement with the perpetrators.
6) Lodge complaints with regulatory bodies
If you suspect mishandling of your data, consider filing a complaint with:
- The Federal Trade Commission (FTC) at reportfraud.ftc.gov
- Your state’s attorney general or data protection authority
Registering complaints with regulatory entities adds pressure on the company to be accountable and can aid in preventing future misuse of your data.
DOWNLOAD THE FOX NEWS APP HERE
Kurt’s concluding remarks
The breach at Tea, a platform that pledged privacy and provided women with a safe space to share, exemplifies the failure to prioritize data protection. While breaches on other apps could potentially be contained, one where users disclose sensitive information poses genuine risks. The immediate aftermath of the breach has already seen victims facing harassment, and the situation may escalate further.
Do you believe that apps handling sensitive data should adhere to stricter security standards? Share your thoughts with us by contacting us at Cyberguy.com/Contact.
Sign up for my FREE CyberGuy Report
Receive top tech tips, urgent security alerts, and exclusive deals directly in your inbox. Plus, gain instant access to my Ultimate Scam Survival Guide – all for free when you subscribe to my CYBERGUY.COM/NEWSLETTER.
Copyright 2025 CyberGuy.com. All rights reserved.
Kurt “CyberGuy” Knutsson is an award-winning tech journalist with a profound passion for technology, gadgets, and gear that enhance life. He contributes to Fox News & FOX Business, appearing on “FOX & Friends” in the mornings. Have a tech query? Sign up for Kurt’s free CyberGuy Newsletter, share your insights, suggest a story, or provide feedback at CyberGuy.com.





